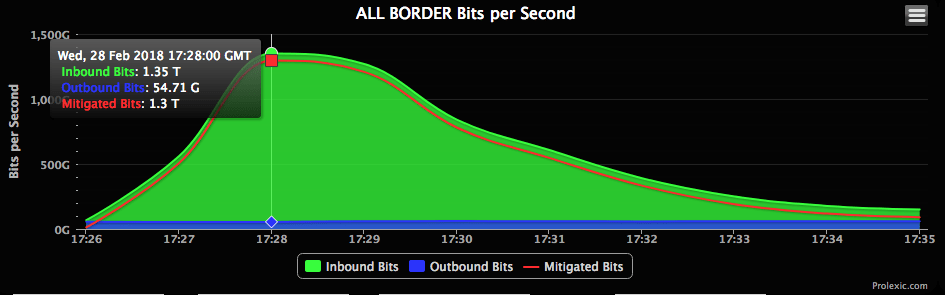
If you already read my DDOS Introduction blog post you know that Volumetric attacks are measured with a magnitude of bits per second. In the above picture, you can see the peak magnitude is 1.35 Terabytes per second. Imagine for a second that this volumetric attack would come to you. It will consume your bandwith with no time. In my opinion the best solution to this type of huge volumetric attack would be a cloud mitigation service.
Big brother of the attack types : Volumetric attacks
Volumetric ddos attacks are the most devastating ones amongst those three. It is because similar to a real flood that will put everything down along its way, Volumetric attacks are also have nearly the same characteristic.
Sooner or later this flood will hit your coasts too. Therefore better be prepared then sorry. In my early post i mentioned some of the precautions. This time i will try to explain the characteristics of a Volumetric attack. In addition to that some common volumetric attack types and their respected mitigation strategies.
Characteristic of a Volumetric attack
Since main objective of a volumetric attack is saturating the link, attackers would send great amount of traffic to that link. Attackers will generate this traffic via reflection , amplification or botnets.
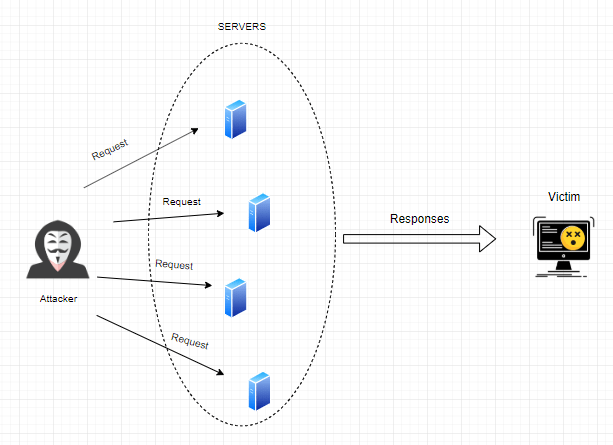
Above illustration not only shows the generic diagram of a volumetric attack but also shows my perfect drawing skills. All jokes aside, this is the generic scheme of a volumetric DDOS attack. Attacker will send requests or commands to servers on the internet. Source ip adresses are genrally spoofing . In Amplification attacks; attackers take leverage of abusive responses. They will send a request to a server and server will generate a response with greater then the request. As you alread guessed responses will go to victim’s ip adresses. This will result a congestion.
Common volumetric attack types
- Memcached Amplification
- DNS Flood
- DNS Amplification
- NTP Amplification
- HTTP Flood
- SYN Flood
- ACK Flood
- CharGEN Amplification
How to defend against Volumetric DDOS attacks ?
First we need to detect volumetric attacks. Let’s say you have a traffic pattern of 500M to 700M and have a bandwith of 1G. It means that anything bigger then 700M and lesser then 1G is an anomaly. 1G bandwith and 1G traffic equals to saturation and service disruption that is why i did not mention it. In ISP or Cloud Mitigation services, anomalies are detecting via Flow data. Depends on the DDOS vendor in the ISP countermeasures are similar. Some of them are rate limiting, port blocking, authentication sources etc. Volumetric attacks are generally mitigated from ISP or Cloud Mitigation Services. Because they have much more bandwith then you have. Also you do not want that traffic come to your front door.
Second line of defense on premise ddos devices. If our ISP or Cloud Mitigation service provider fails to stop the attack or did not respond it in time we could always use and mitigate the attack with on premise ddos devices. They gave us availability. Since these devices are generally placed inline we have better weapons. For example we can analyse the traffic in realtime and use a filter while under attack. Of course we can do that in cloud too. But using an premise device gives you better control on the defense.
Having an inventory of the ip adresses and not used ones are helpful in here. Because if we only announce used ip adresses to the outer world we will reduce the risk of unwanted respond traffic to that ip adresses.
As i mentioned from my previous blog post having a solid playbook to response ddos attacks is a must.
Now you see me, now you don’t!
Volumetric attacks are also good cover-ups. When your house is on fire you do not check your seperate key or backdoor lock. Attackers may use volumetric attacks to hide penetration attempts. Security teams focus may be on resolving the congestion but while the focus is on there your assets or sensitive data may be infiltrating.
As final words i will leave some useful links below there.

