I was planning to write this script for a long time but due to real life responsibilites i keep delayed it. Finally last weekend i got some time to finish and test the script. I wrote the script by pieces on weekends and after work. It is not a complicated script but it does its job well.
As a Network and Security Engineer’s perspective, daily tasks are a part of our routines. Whenever you can automate your repetitive tasks you should do it! Writing a script feels like solving a sudoku to me. It oils the gears in my head. Anyway, automation solves more then one problem. It gives you more time to focus what really matters. It sharpens your analytical thinking and problem solving skills. Long story short lets get back to topic and serve this blog post its purpose.
Fortibulk
Fortibulk is a python based Firewall bulk configuration automation script. It reads the configuration data from text files, processes them and writes it in to firewall. In order to work it properly it needs some data.
Dependencies
You must have the below libraries;
import paramiko
from paramiko_expect import SSHClientInteraction
from getpass import getpass
from tqdm import tqdm
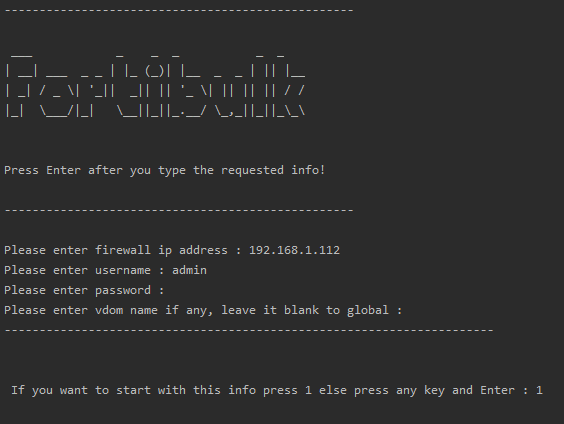
from art import *Fortibulk needs to have at least one of the three files in the picture above. You can combine its functionality by using all three functions or just the one you need. There needs to be some formatting for the files too.
Prerequisities
addresses.txt
If you want to configure address objects you need to have a file called addresses.txt in the same folder with script. In this text file you should prepare your address objects like the below syntax.
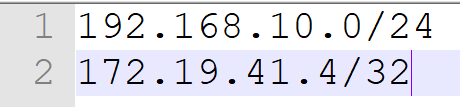
Every line has one network address object reference. Script takes it and splits it into two parts as network ip and subnet. After that it will use this notation as its name. For example we have a /24 network. Script will push it as “192.168.10.0/24” name of the address object and 192.168.10.0 255.255.255.0 as the objects itself. Every line must have only 1 object. there is no max limit of this.
services.txt
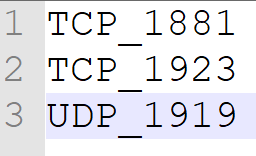
This part is for custom services objects. For example if you need to create custom services like TCP_1923 , TCP_1881 etc. In this function you can set your services as TCP or UDP. Example notation is below.
policy.txt
Lastly we have policy.txt files. This one is the most useful one amongst three in my opinion. It creates and adds the policies before the implicit deny policy and after all the policies. Its use case can vary from the first setup of the firewall to migration scenarios. Like its friends it needs to have a proper txt file. Example syntax for the text file is in below image.
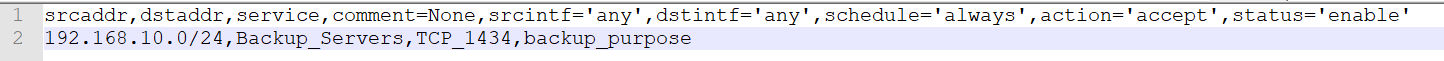
Click the image for readable size
Every policy must be written in one line. At least 3 data must be given. Those are Source address, Destination address and Service. Your source address , destination address or service must be created on the firewall before hand. Otherwise it will not work. If you want to add more details to your rules feel free to provide details. For example you can comment your rules as ticket numbers in your organization that refers to the rule. You can comment it to help remember why you wrote this rule in the first place. You can also specify source interface , destination interface and schedule options.
In the first line i gave the example syntax and predefined values. If you just want to provide basics script will handle rest with the values in the picture.
If everything goes well you will have the below output.
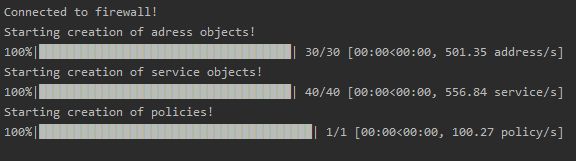
You can get the full source code from here
If you have any questions or suggestions just comment it here or write me via Linkedin.


whoah this blog is fantastic i really like studying your articles.
Stay up the great work! You already know, many persons are searching
around for this info, you can help them greatly.
The information is incredibly intriguing.
Thanks, James
Sustain the good work and generating the crowd!
Thanks Brian!
Long time supporter, and thought I’d drop a comment.
Your wordpress site is very sleek – hope you don’t mind
me asking what theme you’re using? (and don’t mind if I steal it?
:P)
Keep up the good work– and hope you all take care
of yourself during the coronavirus scare!
Thanks for supporting Justin. My theme is Norge from Quantica Labs. Since your site is not related with technology or a blog i edited that part. Wish you best of luck about your site and healthy days for coronovirus disease. Be safe!