Layer seven attacks abuse the application layer processes. This type of attack is highly targeted. Because of its nature it generally used against high value targets such as financial institutes or e-commerce firms.
This is last post of my DDOS Introduction Series. Full post series are below.
- Nightmare of the Security World – DDOS
- The Art of War
- Volumetric DDOS Attacks
- DDOS Protocol Attacks
- DDOS Application Layer Attacks (a.k.a. L7 Attacks)
According to Alex Cruz Farmer , Product Manager for Security at Cloudflare, OSI Layer Seven attacks are increasing from 160 attacks per day up to over 1000 attacks. Original blog post is here.
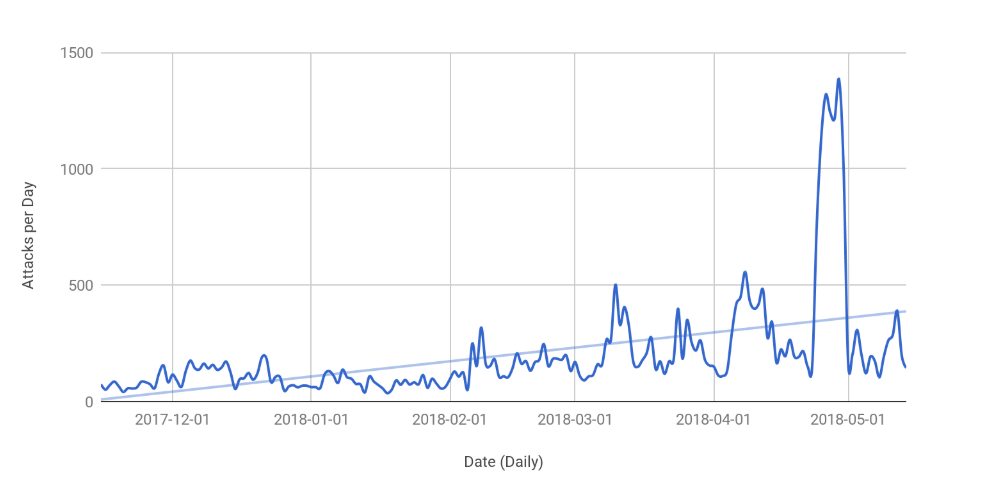
Attack rates are increasing because it is the hardest attack type to defend against. There are some known attack types and corresponding mitigation strategies but this category is very open to zero day attacks. A motivated attacker can analyse your system and make a custom tailor layer seven attack.
Well known attack types
Let’s take HTTP as an example, HTTP is a request-response protocol. If you want abuse the protocol to attack a target you need to manipulate the process or packets. Some of the well known layer seven attacks are based on the HTTP protocol. For instance; Slowloris , Slow Read , Slow Post and HTTP Flood. This is to say, what happens if the attackers adds an encryption flavor to its attack vector? This changes lots of things in the defender site since the traffic is no longer clear text. Now the traffic must be opened in order to mitigate against.
As you can see from the above example little changes can make big impacts on the layer seven attacks. Another example of why i said this type is the hardest attack type to defend against is BGP Hijacking. This is no different then stealing your mails or letters from your postbox.
On the internet traffic is routing from source to destination with a protocol called BGP. Attackers are falsely announcing an IP prefix to the Internet. All the traffic that is destined to those prefixes will go to attackers. There are lots of real world BGP Hijacking examples. In 2010, Pentagon traffic was routed through Beijing in another BGP hijacking example. In future i may have a dedicated blog post about BGP Hijacking.
Mitigation strategies
There are two main mitigation strategies against Application layer attacks. First one is rate-limiting. You must filter the requests. A web application firewall along with a on premise ddos solution is a good combination to address this. Second mitigation strategy could be authenticating the sources. If you authenticate the sources you can verify the request is coming from a legitimate client.

